Data Protection Standards
Introduction
Today, data protection security and information safety are strategically important in every sector. With the development of technology, protecting data requires a more complex and multi-layered approach against cybersecurity threats. Therefore, data protection standards and frameworks guide organizations to handle this challenging task.
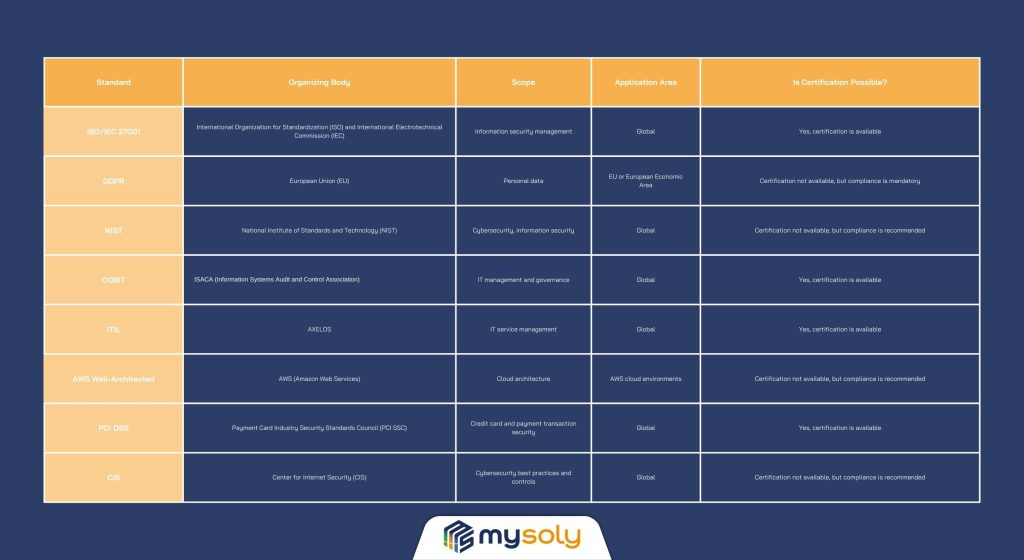
Security and governance standards such as ISO/IEC 27001, GDPR, PCI DSS, NIST Cybersecurity Framework, COBIT, ITIL, and AWS Well-Architected offer comprehensive solutions for different requirements and sectors. That’s why, they play a critical role in ensuring and maintaining information security.
This article will examine how these contribute to data protection standards and security management processes.
1. ISO/IEC 27001
ISO/IEC 27001 is an international standard that defines the requirements for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). Also, this system helps identify and control security risks while securing an organization’s operational processes. In addition, ISO/IEC 27001 offers a holistic approach that covers technical and managerial controls.
The standard includes three main principles to ensure information security:
- Confidentiality
- Integrity
- Availability
On the other hand, factors like accountability, access control, reliability, and safety also support information security.
An ISMS that meets ISO/IEC 27001 requirements protects information confidentiality, integrity, and availability through a risk management process. It also assures relevant parties that risks are being managed properly.
ISO/IEC 27001 certification involves an independent audit process. Also, this certification proves that an organization’s ISMS meets setup and implementation standards.
2. GDPR
The General Data Protection Regulation (GDPR) came into effect in May 2018. It introduced a set of rules on protecting the personal data of EU citizens. This regulation also applies to companies outside the EU. Each organization processing the data of EU citizens must comply with GDPR. Its goal is to protect individual data rights and prevent data breaches.
GDPR includes seven key principles that regulate data processing:
- Lawfulness, Fairness, and Transparency
- Purpose Limitation
- Data Minimization
- Accuracy
- Storage Limitation
- Integrity and Confidentiality
- Accountability
Besides, GDPR grants individuals several rights over their data. These include the Right to Access, Right to Rectification, Right to Erasure (Right to be Forgotten), Right to Data Portability, Right to Object to Processing, and the Right against Automated Decision-Making.
Organizations must continuously review and document their data protection and privacy policies. So, they must maintain a system demonstrating GDPR compliance during potential audits. Regular internal audits and Data Protection Impact Assessments (DPIA) should also be conducted.
On the other hand GDPR includes serious penalties for violations. Depending on the nature of the breach, companies can face fines of up to 4% of their global annual revenue or €20 million, whichever is higher.
GDPR has played a crucial role in shaping data privacy laws globally. While no official GDPR certification exists, independent certifications help ease the compliance process.
3. NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) in the USA developed the NIST Cybersecurity Framework. This framework helps organizations manage cybersecurity risks. While it was created for critical infrastructure sectors, it is also useful for all types of organizations. In addition, the flexible and adaptable nature of the NIST Framework guides organizations to improve their current cybersecurity practices.
The framework, which first appeared in 2014 and was updated in 2018, remains one of the most widely adopted security frameworks in the US. And its goal is to raise awareness of cybersecurity risks, define strategies to manage them, and improve security practices.
It provides the necessary building blocks for cybersecurity management in five main functions:
- Identify
- Protect
- Detect
- Respond
- Recover
The NIST Framework divides security maturity into four categories: Partial, Risk-Informed, Repeatable, and Adaptive. As a result, these layers help organizations assess and improve their cybersecurity posture.
4. COBIT (Control Objectives for Information and Related Technologies)
ISACA (Information Systems Audit and Control Association) developed COBIT to manage and control information technology processes. COBIT helps organizations manage IT processes effectively. In addition, it optimizes performance and manages risks.
Its main purpose is to build a strong bridge between business needs and IT governance. So, IT processes become more transparent, manageable, and trackable. On the other hand, COBIT is especially useful for organizations undergoing digital transformation. The framework helps them meet the challenges of IT compliance, regulation, and governance.
COBIT 5 appeared in 2012. However, by 2019, the focus on compliance had changed, especially with the adoption of GDPR data protection laws in Europe. These regulations, enforced in spring 2018, led ISACA to update COBIT’s governance principles to meet new data protection standards.
5. ITIL (Information Technology Infrastructure Library)
ITIL is a framework that defines the best practices and processes for IT service management. In particular, it aims to improve the quality of IT services, reduce costs, and increase customer satisfaction. The UK government developed ITIL in the 1980s. Since then, it has been adopted worldwide and has become an international standard in IT service management.
It is recognized as a global standard because it is based on practical application rather than theory. Companies of all sizes and industries can easily adapt ITIL. It wasn’t created for any specific industry. So, IT groups in manufacturing, service, public, or IT sectors can quickly implement it.
ITIL consists of several components. As a result, it helps organizations manage IT services more efficiently and effectively.
6. AWS Well-Architected Framework
The AWS Well-Architected Framework is a guide that outlines best practices for cloud-based architectures. It includes critical principles regarding data protection standards. Also, it includes key questions that help assess if an architecture follows cloud best practices, with a focus on data protection and security.
The AWS Well-Architected Framework provides a comprehensive approach to data protection standards. Also, it helps organizations securely manage their data. Core components such as data encryption, access control, backups, security, compliance, and data lifecycle management are fundamental parts of AWS’s data protection standards. Therefore, it is possible to consider the AWS Well-Architected Framework a standard related to data protection.
7. PCI DSS
PCI DSS (Payment Card Industry Data Security Standard) is a security standard to ensure the safety of payment card data. This standard globally safeguards cardholder data. Also, it establishes the rules that all organizations in card transactions must follow. Any organization that processes, stores, or transmits credit card data must comply with this standard.
The Payment Card Industry (PCI) Security Standards Council created PCI DSS in 2006. The standard aims to protect credit card data from unauthorized access and theft. Major card networks such as Visa, Mastercard, American Express, Discover, and JCB support the standard. And PCI DSS requires compliance from every organization that processes transactions through these networks. It details the technical and operational requirements to ensure the security of card data.
Compliance with PCI DSS is maintained through regular security assessments and audits. This compliance helps organizations protect their legal and commercial reputations. Also, it enhances customer trust and reduces the risk of potential data breaches. Thus, PCI DSS is of critical importance for all organizations in payment card transactions. Through certification processes and regular security evaluations, card data is processed, stored, and transmitted securely.
8. CIS (Center for Internet Security)
CIS (Center for Internet Security) is a globally famous organization in the field of cybersecurity. It aims to help public and private sector organizations combat cyber threats. CIS consists of a volunteer community of security experts.
One of CIS’s most popular products is CIS Benchmarks. It provides configuration standards for various systems and software aimed at minimizing security vulnerabilities. And, organizations can use these benchmarks to securely configure their systems and protect against cyber threats. Moreover, many sectors worldwide have adopted and applied CIS Benchmarks.
Another important product is CIS Controls. It is a series of prioritized actions that help organizations strengthen their defenses against cyber threats. CIS Controls offer a practical and effective roadmap for organizations looking to improve their cybersecurity. Also, it is applicable to a wide range of organizations, from small businesses to large enterprises.
On the other hand, CIS operates with a community-focused approach. So, security experts, academics, and IT professionals continuously contribute to updating the standards developed by CIS. This collaboration ensures that CIS’s solutions remain current and effective. CIS continues its efforts to raise security awareness and make the cyber world a safer place.
Conclusion
Data protection standards and information security have become indispensable elements, not only as technical requirements but also as essential components of business continuity and compliance. In particular, frameworks such as ISO/IEC 27001 and the AWS Well-Architected Framework provide significant support in helping organizations shape their security policies. Moreover, they help organizations build resilience against cyber threats while ensuring that legal compliance requirements are met. Therefore, effectively implementing one or more of these standards is one of the strongest ways to establish a secure digital infrastructure and, in turn, combat future cyber threats.
At Mysoly E-learn Bv, we place the utmost importance on ensuring these data protection standards. In addition, we are constantly improving our information security and compliance processes. Also, we are committed to implementing the best practices in this field. Our goal is to complete our certification processes quickly so that we can provide our customers with secure and compliant services.