News, articles, tips & tricks
AllAbout CompanyAI Based Multilingual-LMSAI updates and innovationsAPI IntegrationApplication DevelopmentBuild Performance, Frontend ToolsCI/CD - AutomationCloud TechnologiesCompanyEdtech TrendsEducation TechnologyEventsGenerative AIIndustryLarge Language ModelsLearning and Development (L&D)LMS Buyer’s GuideLMS OptimizationLMS SolutionsNews and Trends About AINews and UpdatesSoftware SecuritySoftware TechnologiesTips & Tricks
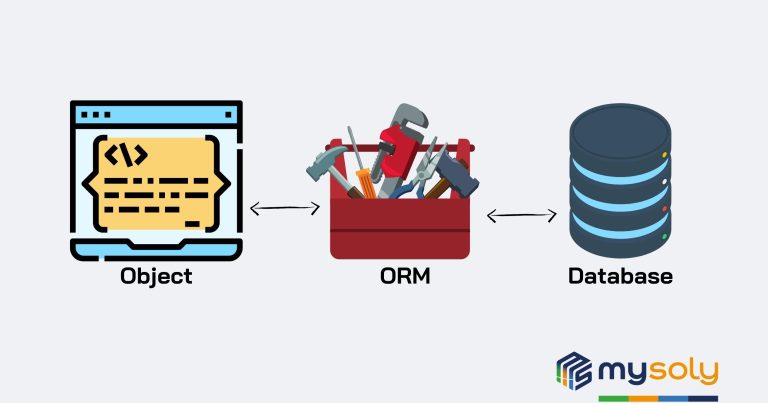
Object-Relational Mapping (ORM) is a programming technique used to convert data between incompatible systems. ORMs allow developers to interact with a database using the programming language’s objects, rather than writing complex SQL queries. This simplifies CRUD operations and provides an abstraction layer over the database, making development easier and more maintainable.
It is more important than ever to protect user data from cyberattacks today. As we addressed in the article “How to Protect Your Data Against Cyberattacks,” many strategies, including securing networks, using firewalls, and employing encryption, are essential to ensuring data protection. Although these techniques provide a comprehensive approach to cybersecurity, one important component is frequently missed. It is the secure storage of user passwords.
Cookies and Local Storage are two important technologies in web development. Cookies are small text files saved in the user’s browser. Websites generally use cookies to manage user sessions, store user preferences, and track user activity. On the other hand, local storage is a solution by modern browsers that can store larger data sets. These two technologies are indispensable for improving the user experience and increasing the functionality of websites.
Today, data protection security and information safety are strategically important in every sector. With the development of technology, protecting data requires a more complex and multi-layered approach against cybersecurity threats. Therefore, data protection standards and frameworks guide organizations to handle this challenging task.
Explore how GDPR safeguards personal data in the Netherlands. From crafting clear privacy policies to swift breach responses, we dive into its tactical role. Plus, discover how AWS bolsters data security. Dive in for expert insights!
It’s important to remember that the security of your data in the cloud is only as strong as the measures you put in place to protect it. Cybersecurity attacks are a trending topic, and it’s crucial to stay informed about the latest threats and how to prevent them.