Secure Password Storage – Basics to Human Behavior
Introduction
It is more important than ever to protect user data from cyberattacks today. As we addressed in the article “How to Protect Your Data Against Cyberattacks,” many strategies, including securing networks, using firewalls, and employing encryption, are essential to ensuring data protection. Although these techniques provide a comprehensive approach to cybersecurity, one important component is frequently missed. It is the secure storage of user passwords. Thus, we will focus on the fundamentals of secure password storage. We will also look at the mathematical principles of methods such as salting, hashing, and HMAC. In addition, we will explore how these techniques can effectively secure passwords against common attacks.
Table of Contents
Basics of the Secure Password Storage
When storing passwords, we don’t save them as plain text. Instead, we use hashing to transform the original password into a fixed-length string of characters. This hashed string is unique to the password. And, even small changes in the input create completely different hashes.
Hashing is a one-way process. It means you can’t take the hashed string and reverse it to figure out the original password. Hashing has an irreversible design, unlike encryption, which you can undo with a decryption key.
Hashing always produces a fixed-length output, no matter the size of the input. For example, you can hash both a single letter and a 12-page document into a string of the same length.
Example:
- The letter “a” becomes:
ca978112ca1bbdcafac231b39a23dc4da786eff8147c4e72b9807785afee48bb
- A multiple-page document might become:
6e340b9cffb37a989ca544e6bb780a2c76234d849b423388edc2c2b01d50c5d3
Even though the inputs are very different in size, the resulting hash is always the same length.
Hash functions create a huge number of possible outputs. For example, SHA-256 produces 2^256 possible hashes. It would take an incredibly long time—even with today’s computers—to figure out the original input by guessing every possible combination. This makes reversing hashes impossible.
Common Hashing Algorithms
There are different algorithms and mechanisms for password hashing and message authentication. Some are stronger than others and have specific use cases.
MD5
This algorithm used to be popular. However, it is less safe now since hackers found ways to create collisions—when two different inputs create the same hash.
MD5 is a widely-used cryptographic hash function that produces a 128-bit hash value. This value is typically shown as a 32-character hexadecimal number. It produces a fixed 16-byte output (128 bits = 16 bytes).
Math Behind it:
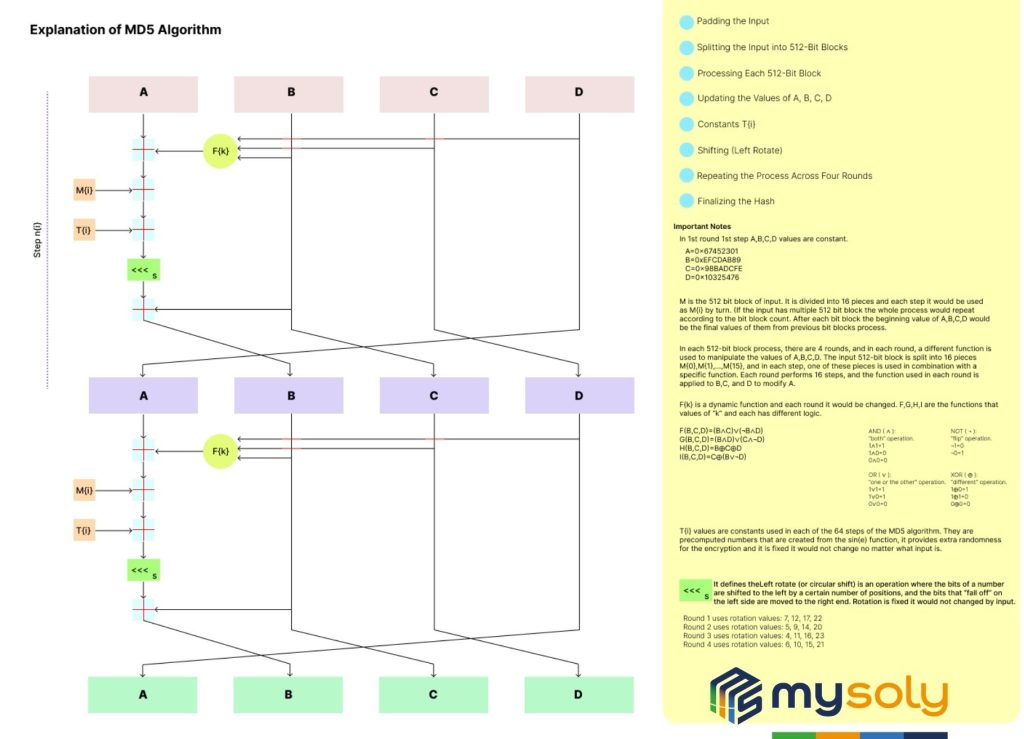
Explanation of MD5 math
SHA-256
This is part of a more secure family of hash algorithms. SHA-256 is much harder to break than MD5.
Math behind it:
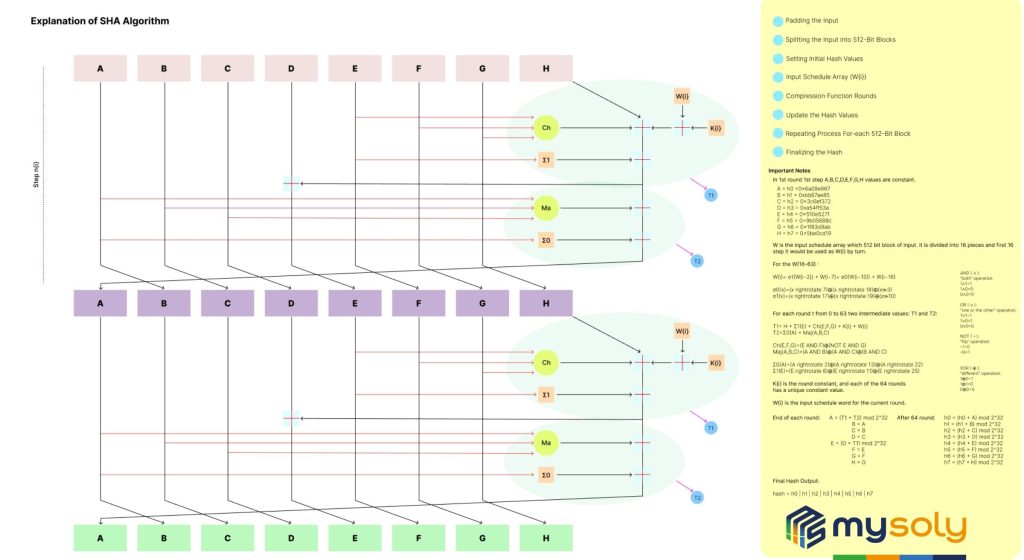
Explanation of SHA math
bcrypt and Argon2
These are modern algorithms specifically for password hashing. They are slow by design. This makes it harder for hackers to guess passwords through brute force.
Process Schema:
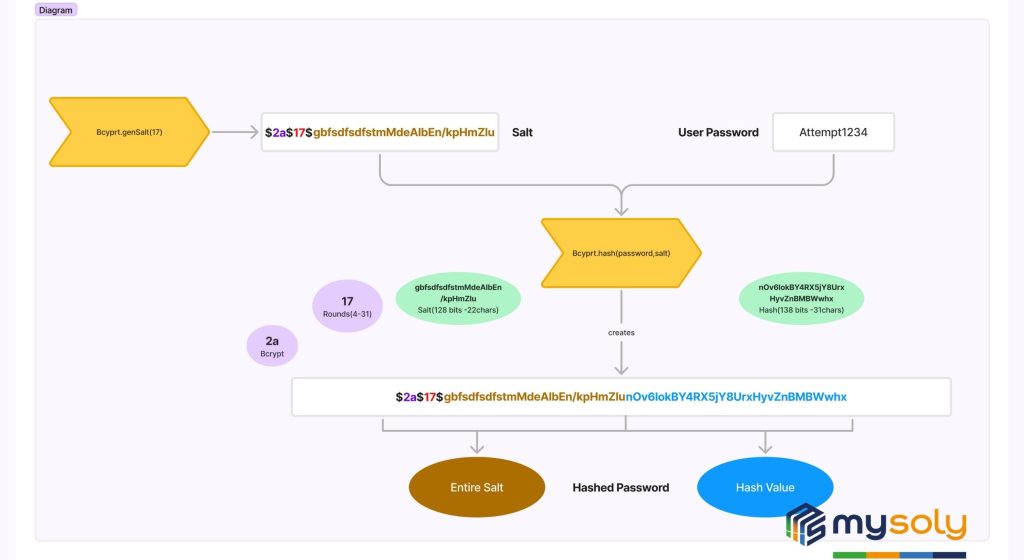
Process Schema of Bycrpty
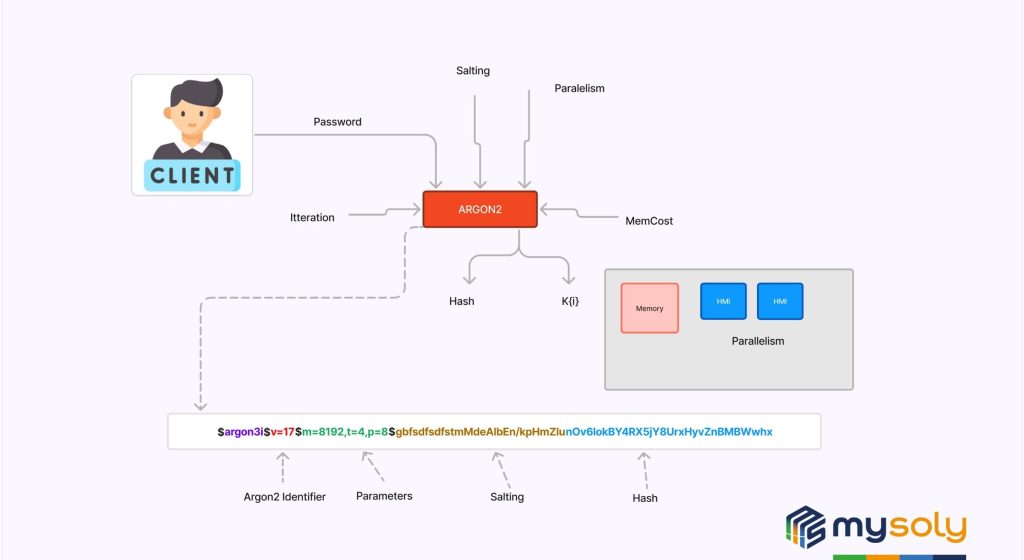
Process Schema of Argon2
HMAC
HMAC (Hash-based Message Authentication Code) is a mechanism to provide message authentication, not just a hash function. It combines a cryptographic hash function with a secret key to ensure the integrity and authenticity of a message. You can combine it with a password to add an extra layer of security.
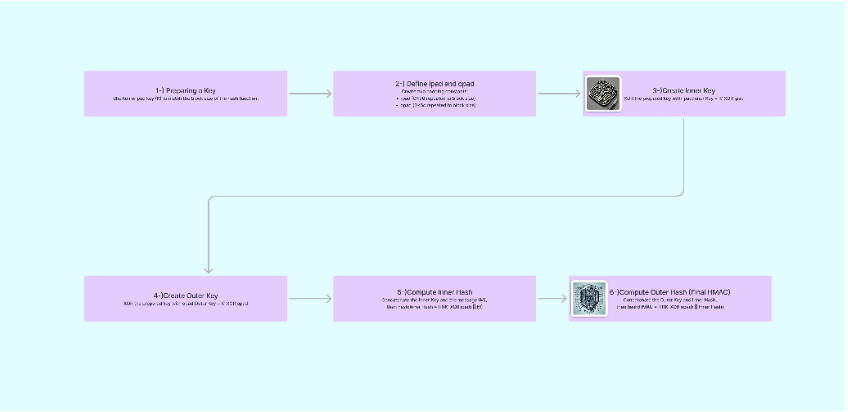
Process Schema of HMAC mechanism
Using HMAC with SHA-256 (called HMAC-SHA256), you can create an even more secure hash that is much harder to break.
Understanding Hash Reversibility
Hashes are hard to reverse. Here’s why:
Collision Resistance:
Developers build hashing algorithms to avoid creating the same hash from two different inputs. This helps keep data secure.
Too Many Possibilities:
For a hash like SHA-256, there are so many possible outcomes that even trying to guess the original input would take forever, making it impossible for hackers.
Input Size Doesn’t Matter:
Whether you hash a small input like a single letter or a large input like a document, the result is always the same length. This means you can’t figure out the size or content of the original data from the hash alone.
Explanation of Salting
Salting adds extra security to password hashing. It works by adding a random value, called a salt, to the password before hashing. As a result, even if two people use the same password, their hashes will be different because they each have a unique salt. Therefore, salting strengthens secure password storage.
Registration: When a user signs up, he/she creates a password. At this point, the system generates a unique, random salt specifically for this password. The system combines the user’s password with the salt. As a result, it becomes a “salted” password. The salted password is hashed, producing a unique hash that is difficult to reverse-engineer. Both the salt and the hash are stored securely in the database.
Login Attempt: When a user logs in, they enter their password. The system retrieves the salt from the database and combines it with the password. Then, it hashes the combination again. As a result, the system ensures security before granting access.
Hash Comparison: The system compares the newly generated hash with the stored hash from registration. The system grants access if the hashes match, confirming the user’s password is correct. If not, the login attempt fails.
Example:
If two users have the password “attempt123”:
- User 1 salted hash might look like: 0x32a7d…
- User 2 salted hash might look like: 0x84f1b…
The salt makes it harder for attackers to use precomputed lists of password hashes (known as rainbow tables) to crack passwords.
Common Attacks on Passwords
Even though hashes are secure, hackers have found ways to try to break them. Here are some common attacks:
Rainbow Table Attacks
These use precomputed tables of password hashes to guess a password. Salting makes this attack much harder, as the salt adds extra complexity to the hash.
Brute-force Attacks
Hackers try every possible combination of characters until they find the correct password. So, using slow hashing algorithms like bcrypt and Argon2 can help protect against this.
Dictionary Attacks
This attack uses common words or phrases to guess passwords. It’s more successful when users choose weak passwords like “123456” or “password.”
Best Practices for Storing Passwords
Use HMAC with a Secret Key
- Combine the user’s password with a secret key stored in your environment settings (e.g., env.config). By using HMAC, you add extra security before hashing the password. As a result, even if attackers access the database, they can’t easily break the password without the secret key. In addition, this method strengthens overall protection.
Apply Salting to the User’s Password
- Before hashing, generate a unique salt for each user and combine it with their password. The salt ensures that even if two users have the same password, the resulting hashes will be different. Salting is crucial to preventing attacks like rainbow tables as it ensures that precomputed hashes are ineffective.
Use Secure Hashing Algorithms like bcrypt or Argon2
- After salting, use a secure hashing algorithm like bcrypt or Argon2 to hash the password. These algorithms are designed to be slow. So, it is difficult for attackers to brute-force passwords. In addition, bcrypt and Argon2 are resistant to common attacks and are common for secure password storage.
Multi Hashing
- Multi-hashing involves hashing the password twice using a cryptographic algorithm like SHA-256 or SHA-512. This adds an extra layer of protection by making it harder for attackers to reverse-engineer the original password, even if they discover the first hash. It works by applying the hash function once, and then hashing the result again.
Example:
Hash the password once with SHA-256:
hash1 = sha256(password)
Then hash the result:
finalHash = sha256(hash1)
This practice is more effective when combined with salting to prevent patterns in the hashing process from being exploited by attackers.
The Weakest Link: Human Behavior
Despite robust security measures like hashing and salting, humans remain the weakest link in the security chain. The main reason is predictable behavior: users often choose weak, simple, or commonly used passwords like “123456” or “password,” and tend to reuse them across multiple platforms. This behavior greatly increases vulnerability to attacks such as credential stuffing or brute-force.
While technical methods help secure password storage, the predictability of human choices undermines these protections. It emphasizes the need for better user education on password practices and the use of strong, unique passwords.
Conclusion
Secure password storage is essential in protecting user data from hackers. By using modern hashing algorithms, adding salts, and following best practices, you can significantly reduce the chances of password hacking. For security, newer methods like passwordless authentication may further improve protection. But for now, using secure hashing techniques remains the foundation of good password storage.